What are the different types of firewalls and how do they work in network security?
Firewalls are essential cybersecurity tools that act as barriers between trusted and untrusted networks. There are several types of firewalls, each with unique functionalities—from packet filtering to deep packet inspection, and cloud-based filtering. Understanding the various types like Packet-Filtering Firewalls, Stateful Inspection Firewalls, Proxy Firewalls, Next-Gen Firewalls, Software, Hardware, and Cloud Firewalls helps organizations choose the best protection method based on their security needs and infrastructure design.

Table of Contents
- What Is a Firewall in Cybersecurity?
- Why Are Firewalls Important?
- 8 Major Types of Firewalls Explained
- Comparison Table: Types of Firewalls
- Which Firewall Is Right for You?
- Conclusion
- Frequently Asked Questions (FAQs)
In today’s hyper-connected digital world, firewalls play a crucial role in protecting organizations and individuals from cyber threats. Whether you're running a data center, managing a business network, or just using the internet at home, firewalls serve as the first line of defense. But did you know there are several different types of firewalls—and each serves a unique purpose?
In this blog, we’ll break down the most important types of firewalls, how they work, their strengths, and when to use each. This guide is ideal for IT professionals, cybersecurity students, or anyone trying to secure their network.
What Is a Firewall in Cybersecurity?
A firewall is a network security system that monitors and controls incoming and outgoing traffic based on predefined security rules. It acts as a barrier between a trusted internal network and untrusted external networks (like the internet), blocking malicious data packets and unauthorized access.
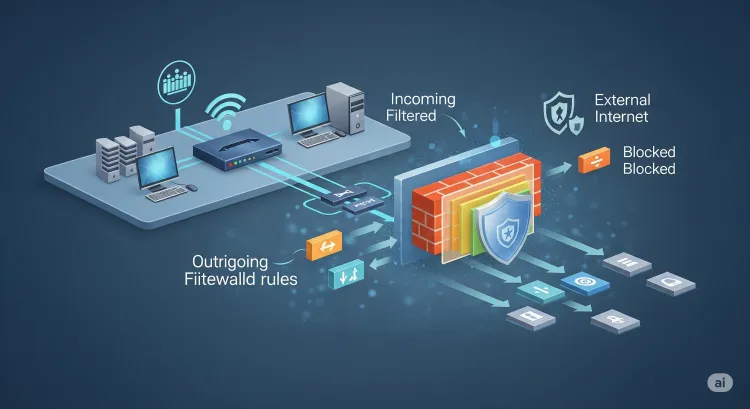
Why Are Firewalls Important?
-
Prevent unauthorized access to sensitive data
-
Control traffic flow and user behavior
-
Detect and block malicious threats
-
Protect internal systems from external attacks
-
Maintain compliance with data protection regulations
8 Major Types of Firewalls Explained
The firewall landscape has evolved significantly over the years. Here’s a deep dive into the major types of firewalls used in cybersecurity today:
1. Packet-Filtering Firewalls
Function: Filters data packets based on predefined rules like IP addresses, ports, and protocols.
How It Works: At the network layer, the firewall checks the packet header information without analyzing the payload. It allows or blocks traffic based on ACLs (Access Control Lists).
Use Case: Simple and fast filtering at the router level; ideal for basic network protection.
Limitation: Cannot inspect packet content or state—vulnerable to spoofing and certain attacks.
2. Circuit-Level Gateways
Function: Validates TCP handshakes without examining the actual data being transmitted.
How It Works: Operates at the session layer. Once the connection is verified, it assumes that the traffic is safe and allows it.
Use Case: Lightweight solution for session validation; useful when minimal resource usage is desired.
Limitation: Doesn’t inspect the payload, so it may allow malicious data through after session initiation.
3. Stateful Inspection Firewalls (Dynamic Packet Filtering)
Function: Tracks the state of active connections and uses context to evaluate packet legitimacy.
How It Works: Maintains a state table to track every connection. It inspects both the header and part of the payload for ongoing traffic.
Use Case: Widely used in enterprise networks for enhanced traffic inspection.
Limitation: More resource-intensive than packet-filtering firewalls.
4. Proxy Firewalls (Application-Level Gateways)
Function: Acts as an intermediary between users and services, masking internal identities.
How It Works: Intercepts requests and fetches data on behalf of the user. It can filter traffic based on application-level rules (like HTTP, FTP).
Use Case: Great for anonymous browsing and enforcing strong content filtering.
Limitation: Can slow down performance due to deep inspection.
5. Next-Generation Firewalls (NGFW)
Function: Combines traditional firewall capabilities with deep packet inspection, intrusion prevention, and threat intelligence.
How It Works: Operates across multiple layers (from transport to application) using advanced algorithms and AI to detect malicious behavior.
Use Case: Essential for enterprises and SOCs that require comprehensive threat prevention.
Limitation: High cost and complexity in setup and management.
6. Software Firewalls
Function: Installed on individual endpoints (PCs, servers) to filter traffic as per software-based rules.
How It Works: Runs on operating systems and blocks traffic based on policies defined by the user or admin.
Use Case: Ideal for personal devices and internal segmentation within organizations.
Limitation: May consume system resources and is only effective per device.
7. Hardware Firewalls
Function: Standalone physical appliances that protect entire networks at the perimeter.
How It Works: Usually placed between the router and the internet. These devices block or allow traffic based on internal firmware rules and configurations.
Use Case: Suitable for enterprises and large networks that need perimeter-based defense.
Limitation: Expensive and requires professional installation.
8. Cloud Firewalls (Firewall-as-a-Service)
Function: Hosted in the cloud and designed to protect distributed networks and applications.
How It Works: Filters traffic across multiple environments (on-premise, cloud, hybrid) without relying on physical infrastructure.
Use Case: Ideal for cloud-native apps, remote workers, and SaaS environments.
Limitation: Internet-dependent; performance may vary with latency.
Comparison Table: Types of Firewalls
| Firewall Type | Level of Operation | Key Feature | Best Use Case |
|---|---|---|---|
| Packet-Filtering | Network Layer | Fast, basic filtering based on IP/port | Routers, small networks |
| Circuit-Level Gateway | Session Layer | Validates TCP handshakes | Low-resource environments |
| Stateful Inspection | Transport Layer | Context-aware, tracks active connections | Corporate networks |
| Proxy Firewall | Application Layer | Anonymity and content control | Browsing control, app filtering |
| Next-Gen Firewall (NGFW) | Multi-layer | Threat detection + AI-powered inspection | Enterprise security |
| Software Firewall | Host-level | Custom policies for each device | Personal computers, internal segments |
| Hardware Firewall | Perimeter-level | Protects whole networks via physical appliances | Large enterprise networks |
| Cloud Firewall | Cloud-level | Scalable protection across cloud environments | SaaS, cloud-native companies |
Which Firewall Is Right for You?
Choosing the right firewall depends on:
-
Size of your organization
-
Type of applications you run
-
Level of threat exposure
-
Budget and IT resources
For basic home use, a software firewall is sufficient. Enterprises often opt for NGFWs or hardware firewalls, while cloud-first organizations may go with cloud firewalls.
Conclusion
Firewalls are essential to network security, and understanding their types helps in implementing a defense-in-depth strategy. From packet-filtering firewalls to advanced next-gen systems, each firewall serves a unique role in protecting data, devices, and users from cyber threats.
Implementing the right firewall setup can prevent everything from malware to ransomware, phishing, and even zero-day exploits. Stay proactive—because in cybersecurity, prevention is always better than cure.
FAQs
What is a firewall in cybersecurity?
A firewall is a network security device or software that monitors and controls incoming and outgoing traffic based on predefined rules, protecting systems from unauthorized access.
How many types of firewalls are there?
There are primarily seven types: Packet-Filtering Firewalls, Circuit-Level Gateways, Stateful Inspection Firewalls, Proxy Firewalls, Next-Gen Firewalls, Software Firewalls, and Hardware/Cloud Firewalls.
What does a packet-filtering firewall do?
It filters network traffic by analyzing IP addresses, ports, and protocols at the network layer.
How does a circuit-level gateway work?
It validates TCP handshakes to ensure that the session is legitimate without inspecting the data itself.
What is a stateful inspection firewall?
It monitors active connections and uses full session context to allow or block packets.
What is the role of a proxy firewall?
A proxy firewall hides user identities by acting as an intermediary between users and web resources.
What are Next-Generation Firewalls (NGFW)?
NGFWs combine standard firewall functions with deep packet inspection, application awareness, and threat intelligence.
What is a software firewall?
Installed on individual systems, it filters traffic based on user-defined software rules and policies.
How is a hardware firewall different from a software firewall?
A hardware firewall is a standalone device that filters traffic at the network’s perimeter, while software firewalls operate at the host level.
What is a cloud firewall?
Cloud firewalls are hosted in the cloud and protect distributed systems by filtering traffic in cloud-based environments.
Which type of firewall is best for small businesses?
Software firewalls or NGFWs are often ideal for small businesses due to their flexibility and comprehensive threat protection.
Do cloud firewalls replace hardware firewalls?
Not always. Cloud firewalls are best for cloud-based infrastructures, while hardware firewalls protect on-premise networks.
Can a firewall block malware?
Yes, especially Next-Gen Firewalls with deep packet inspection and threat detection capabilities.
Is a proxy firewall secure?
Yes, it adds an extra layer of protection by masking internal network identities.
Why is firewall configuration important?
Improper configuration can leave networks exposed. Proper rules and updates are essential for protection.
Are all firewalls capable of deep packet inspection?
No, only advanced types like NGFWs and some stateful firewalls offer deep inspection.
What’s the difference between IDS and firewalls?
Firewalls block traffic, while Intrusion Detection Systems (IDS) only alert on suspicious activity without blocking it.
Can I use both software and hardware firewalls together?
Yes, combining them creates layered security, enhancing protection.
Are stateful firewalls outdated?
They are still effective but often combined with NGFWs for advanced threat detection.
Is there a free firewall for personal use?
Yes, several software firewalls are available for free for individual users, such as ZoneAlarm and TinyWall.
Can firewalls prevent phishing attacks?
NGFWs and proxy firewalls can help prevent phishing by filtering malicious domains.
What is an example of a hardware firewall?
Cisco ASA and Fortinet FortiGate are well-known hardware firewalls.
Are cloud firewalls scalable?
Yes, cloud firewalls scale easily to meet changing needs of businesses and applications.
How do firewalls affect network performance?
Some firewalls can slightly reduce performance, especially during heavy inspection, but modern solutions are optimized for speed.
Do firewalls protect against DDoS attacks?
Some advanced firewalls offer protection against DDoS, though dedicated DDoS mitigation tools are more effective.
Can firewalls work with VPNs?
Yes, firewalls often work alongside VPNs to provide encrypted and secure traffic tunnels.
Is firewall logging important?
Absolutely. Logs help track threats, monitor activity, and ensure compliance.
Do firewalls require regular updates?
Yes, regular updates ensure firewalls can defend against the latest threats.
Are there AI-powered firewalls?
Yes, many NGFWs now use AI/ML to detect threats based on behavior and anomaly detection.
What are enterprise firewalls?
Enterprise firewalls offer high-performance filtering, logging, and scalability to secure large networks.
Is it safe to rely on cloud firewalls alone?
No, it’s best to use a multi-layered approach including cloud, hardware, and endpoint security.














![Top 10 Ethical Hackers in the World [2025]](https://www.webasha.com/blog/uploads/images/202408/image_100x75_66c2f983c207b.webp)








