Lilu (Lilocked) Ransomware Started Infecting Thousands of Linux Servers Back to Back
A new strain of ransomware named Lilocked or Lilu has affected thousands of Linux-based servers everywhere the world. The ransomware started infecting servers back in period of time however within the last two weeks, the attacks became a lot of frequent.

The very first case of Lilocked ransomware came to light when a user uploaded a ransomware note on ID Ransomware, a website used for identifying the name of ransomware from the ransomware note or demand specified in the attack.
It targets servers and gains its root access. The mechanism behind however it gets access in unknown yet.
According to a Russian forum, bad actors might be targeting Linux-based servers that are running defunct Exim software.
Demand – 0.03 Bitcoin
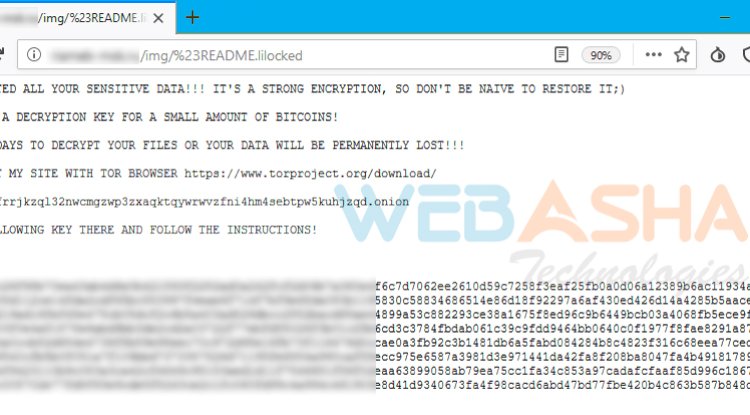
After a server has been attacked, the files are locked with “.lilocked” file extension.
The note accompanied with the encrypted files reads: “I’ve encrypted all your sensitive data!!! It’s a strong encryption, so don’t be naive to restore it;)”
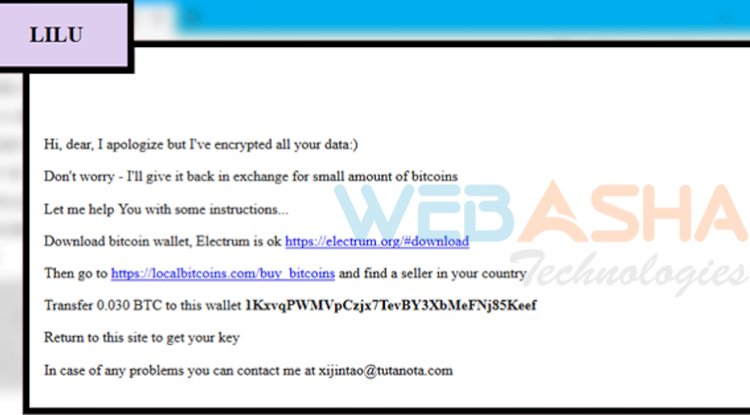
Upon clicking the link in the note, users are redirected to a website on the dark web, prompting them to enter the key in the note. When the affected user enters the key, they are asked to deposit 0.03 bitcoin or $325 in the Electrum wallet to get their files decrypted.
Lilock ransomware does not affect system files but files with extensions including HTML, SHTML, JS, CSS, PHP, INI, and other image formats. Since system files are not affected, Linux systems are running normally.
As per Benkow, a French security researcher, Lilock ransomware has affected 6,700 servers to date. Most of these servers are cached in Google search results. However, the number of infected servers can be far more as there ar several infected Linux servers that don’t seem to be indexed on Google.
Since the mechanism behind the ransomware isn’t well-known yet, there isn’t a security consultive. You might evade this attack by keeping strong passwords and updating the apps as and when security patches arrive.














![Top 10 Ethical Hackers in the World [2025]](https://www.webasha.com/blog/uploads/images/202408/image_100x75_66c2f983c207b.webp)








