How Microsoft Teams Calls Are Being Weaponized to Deploy Matanbuchus Ransomware | Full Guide
In July 2025, cybercriminals began exploiting Microsoft Teams calls to deploy Matanbuchus ransomware through social engineering. Attackers impersonate IT support via Teams, using Quick Assist and PowerShell commands to execute malware. This blog explains how the attack works step-by-step, outlines its impact on businesses, and provides actionable prevention tips like disabling Quick Assist, limiting PowerShell, and training employees to recognize social engineering threats.
Table of Contents
- Attack Flow and Protection Measures
- How the Attack Works – Step-by-Step Breakdown
- Why This Attack Matters
- How to Protect Against It
- Conclusion
- Frequently Asked Questions (FAQs)
A sophisticated cyberattack method now leverages Microsoft Teams calls to deliver Matanbuchus ransomware. This attack bypasses traditional email-based defenses and exploits human trust in real-time communication.
A new and sophisticated cyberattack technique has emerged that uses Microsoft Teams calls as a delivery mechanism for the Matanbuchus ransomware loader. Security researchers have confirmed that attackers are impersonating IT support staff via Teams video calls, convincing victims to execute malicious PowerShell commands. This marks a critical evolution in ransomware delivery tactics, leveraging trusted business collaboration tools.
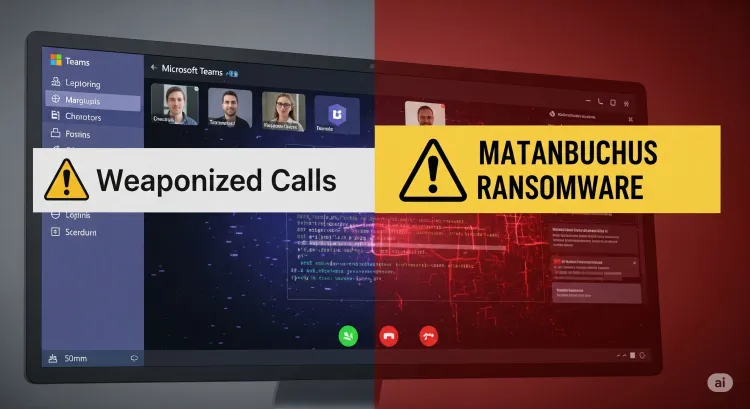
Attack Flow and Protection Measures
| Attack Stage | Description | Recommended Defense |
|---|---|---|
| Social Engineering Call | Impersonating IT via Microsoft Teams | Employee security training and awareness |
| Quick Assist Activation | Convincing users to grant remote access | Disable or restrict Microsoft Quick Assist |
| PowerShell Command Execution | Running commands to install Matanbuchus loader | Monitor PowerShell usage; apply execution policies |
| Loader Deployment | Deploying Matanbuchus 3.0 to execute ransomware or steal data | Endpoint protection, behavior-based detection tools |
| Persistence and Impact | Encrypting files, exfiltrating data | Data backups, incident response planning |
How the Attack Works – Step-by-Step Breakdown
1️⃣ Social Engineering via Teams Calls
Attackers initiate Teams calls posing as IT staff, using urgency and authority to trick employees.
2️⃣ Remote Access via Quick Assist
Victims are guided to enable Quick Assist, giving attackers full remote access to their systems.
3️⃣ PowerShell Command Execution
Once connected, attackers execute PowerShell scripts to silently deploy malware loaders.
4️⃣ Matanbuchus 3.0 Deployment
The loader installs ransomware, remote access tools, or infostealers without triggering traditional antivirus software.
Why This Attack Matters
-
Bypasses Email Security Filters
-
Higher Trust Due to Live Calls
-
Uses Legitimate Windows Tools (Living Off the Land)
How to Protect Against It
-
Train Employees on social engineering threats specific to video conferencing.
-
Disable Quick Assist where not needed using Group Policy or endpoint management tools.
-
Limit PowerShell Usage and monitor unusual command execution.
-
Implement MFA and strong authentication measures for Microsoft accounts.
-
Maintain Regular Backups of critical systems and files.
Conclusion
Weaponizing Microsoft Teams calls is a wake-up call for organizations relying on collaborative tools. Security policies must evolve beyond email filters to address live social engineering attacks.
FAQs
What is the Matanbuchus ransomware?
Matanbuchus ransomware is a malware strain designed to encrypt files and sometimes exfiltrate data from infected systems, demanding payment from victims to restore access.
How does Microsoft Teams get exploited in ransomware attacks?
Cybercriminals impersonate IT support via Teams calls, use social engineering to convince employees to grant remote access, and execute malicious scripts like Matanbuchus.
What is Quick Assist in Windows?
Quick Assist is a Windows tool that allows remote control of a device for troubleshooting, which attackers misuse to deploy malware during social engineering attacks.
How do attackers use PowerShell in these campaigns?
Once remote access is gained, attackers run PowerShell commands to download and execute malicious loaders like Matanbuchus 3.0.
What is Matanbuchus 3.0 Loader?
It’s the latest version of the Matanbuchus ransomware loader used in July 2025 attacks, designed to silently deliver malware on compromised devices.
Why is Microsoft Teams a target for hackers?
Because of its widespread use in business environments and its real-time communication features, which attackers exploit to build trust quickly.
What is social engineering in cybersecurity?
Social engineering refers to manipulating people into revealing confidential information or performing actions that compromise security.
Can Microsoft Teams calls be blocked from unknown contacts?
Yes, organizations can configure Teams policies to limit calls from external users or require verification before allowing new contacts.
What makes this Microsoft Teams attack method different?
It combines video call trust, legitimate Windows tools (like Quick Assist), and script-based malware deployment—bypassing traditional email-based phishing filters.
How can organizations prevent Teams call-based ransomware?
By training employees, disabling unnecessary tools like Quick Assist, limiting PowerShell usage, and monitoring unusual behavior.
Is Matanbuchus ransomware new?
No, but the 3.0 version includes updated delivery mechanisms as seen in the 2025 Microsoft Teams weaponization campaign.
What are living-off-the-land attacks?
These attacks use built-in tools like PowerShell or Quick Assist instead of downloading external malware, making detection harder.
How do you disable Quick Assist in Windows?
Quick Assist can be disabled through Group Policy Editor or endpoint management systems like Intune.
What is the typical ransom demand from Matanbuchus?
Ransom demands vary, but they can range from a few thousand to millions of dollars depending on the target organization.
Does antivirus software detect Matanbuchus?
Some security products may detect parts of the attack chain, but living-off-the-land tactics often evade signature-based detection.
What is Microsoft doing about Teams call-based attacks?
Microsoft regularly updates its security features but also emphasizes user awareness and organizational policies to limit these risks.
Can non-Windows platforms be affected by Matanbuchus?
Matanbuchus primarily targets Windows systems, especially in environments that use Microsoft Teams.
What’s the role of endpoint detection and response (EDR) in preventing such attacks?
EDR tools can help detect unusual script execution, unauthorized remote access, and other indicators of compromise.
How do attackers inflate trust during Microsoft Teams calls?
By impersonating known IT support, using official-sounding language, and creating urgency.
Are there reports of similar Teams call-based attacks before 2025?
Social engineering via video calls has been noted in the past, but its use with ransomware like Matanbuchus 3.0 is a newer development.
What industries are most at risk from these attacks?
Finance, healthcare, education, and tech companies that rely heavily on Microsoft Teams and remote work setups.
How can individuals protect themselves from Teams call scams?
Always verify the identity of unknown contacts, avoid granting remote access without double-checking, and report suspicious behavior.
What happens after Matanbuchus infects a device?
It encrypts files, may steal data, and displays a ransom note demanding payment for decryption.
Can Matanbuchus spread laterally across a network?
Yes, depending on its configuration and permissions, it can move laterally to infect other devices.
Is multi-factor authentication (MFA) helpful against Teams ransomware?
MFA helps prevent account hijacking but does not directly prevent social engineering via live calls.
How does disabling Quick Assist improve security?
It removes one avenue attackers can use to gain remote access without needing to install third-party tools.
Can regular Teams calls be intercepted by attackers?
Not directly, but attackers can initiate calls under false pretenses, tricking users into granting access.
What’s the connection between Teams and PowerShell in this attack?
Teams is used to initiate social engineering, while PowerShell is the tool used to deploy the ransomware payload.
Are small businesses at risk from Teams ransomware?
Yes, especially if they use Microsoft Teams without robust security policies or employee training.
How fast does Matanbuchus deploy after initial access?
Deployment can occur within minutes once remote access is established, making swift detection critical.
Where can I read more about Matanbuchus ransomware?
You can follow updates from cybersecurity blogs, vendors like Microsoft and SentinelOne, and threat intelligence platforms.














![Top 10 Ethical Hackers in the World [2025]](https://www.webasha.com/blog/uploads/images/202408/image_100x75_66c2f983c207b.webp)








