Category: Cyber Security & Ethical Hacking
What is Interlock ransomware and how does it attack Win...
Interlock ransomware is a newly identified threat using double extortion tactics and targeting both Windows and Linux systems, par...
What is blockchain analysis and how is it used to detec...
Blockchain analysis involves tracing and examining cryptocurrency transactions on public ledgers to uncover illicit activities suc...
What are the legal aspects of digital forensics and how...
The legal aspects of digital forensics refer to the laws, policies, and regulations governing the collection, preservation, and pr...
What are the key differences between GDPR and CCPA in d...
Data protection and privacy laws like the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA)...
How to Ensure Compliance with GDPR and Other Global Dat...
Businesses in 2025 must adhere to data protection laws like the GDPR, CCPA, DPDP Act, and others to protect personal data and avoi...
How should companies communicate during a ransomware at...
Effective communication during a ransomware attack is as vital as technical response. When systems are compromised, timely and coo...
Mastering IP Whitelisting | What Are Advanced Strategi...
Discover how to master IP whitelisting with advanced strategies tailored for modern security architects. Learn real-time examples,...
What are the most important Wireshark filters every cyb...
Cybersecurity professionals often analyze large volumes of network traffic, and mastering key Wireshark filters helps them identif...
What are attack vectors in cybersecurity and how do hac...
Attack vectors are the various entry points or methods cybercriminals use to infiltrate networks, systems, or applications. These ...
What is the AppLocker bypass flaw and how can malicious...
A critical misconfiguration in Microsoft’s AppLocker block list allows attackers to bypass application restrictions by manipulatin...
How does IndiaMART use Google Cloud Armor for AI-based ...
IndiaMART, a leading Indian B2B marketplace, strengthened its defenses against DDoS attacks and malicious bots by integrating Goog...
What was the recent Microsoft server hack and how did i...
A major cyberattack exploited a zero-day vulnerability in Microsoft SharePoint servers, affecting nearly 100 organizations worldwi...
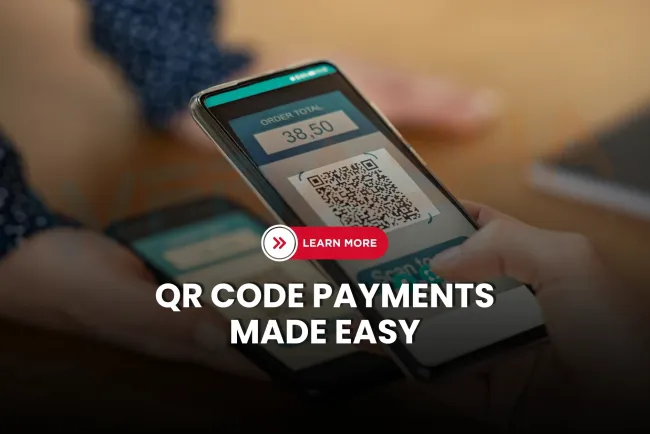
What is 'Scan to Pay' and how does it work step-by-step...
Scan to Pay is a digital payment method where users scan a QR code using a smartphone to instantly pay a merchant. This system use...
How did a weak password lead to the downfall of a 158-y...
A single weak password led to the devastating collapse of KNP Logistics, a 158-year-old UK transport company, after it fell victim...
What is the importance of penetration testing for start...
Penetration testing (pen testing) is crucial for startups in 2025 because it helps detect and fix security vulnerabilities before ...





















![Top 10 Ethical Hackers in the World [2025]](https://www.webasha.com/blog/uploads/images/202408/image_100x75_66c2f983c207b.webp)








