Category: Security News & Threat Intelligence
How to Ensure Compliance with GDPR and Other Global Dat...
Businesses in 2025 must adhere to data protection laws like the GDPR, CCPA, DPDP Act, and others to protect personal data and avoi...
What is the AppLocker bypass flaw and how can malicious...
A critical misconfiguration in Microsoft’s AppLocker block list allows attackers to bypass application restrictions by manipulatin...
How does IndiaMART use Google Cloud Armor for AI-based ...
IndiaMART, a leading Indian B2B marketplace, strengthened its defenses against DDoS attacks and malicious bots by integrating Goog...
What was the recent Microsoft server hack and how did i...
A major cyberattack exploited a zero-day vulnerability in Microsoft SharePoint servers, affecting nearly 100 organizations worldwi...
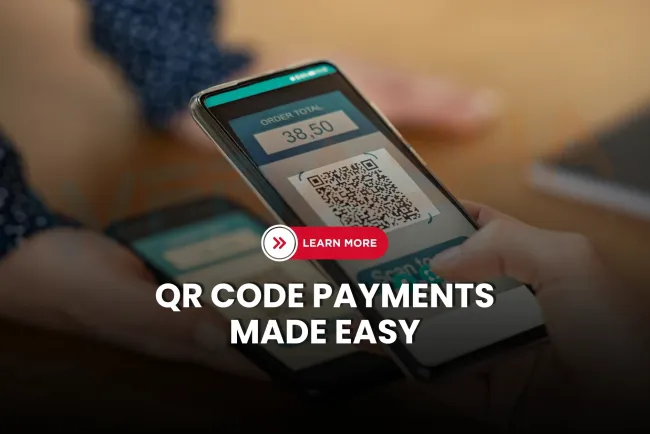
What is 'Scan to Pay' and how does it work step-by-step...
Scan to Pay is a digital payment method where users scan a QR code using a smartphone to instantly pay a merchant. This system use...
How did a weak password lead to the downfall of a 158-y...
A single weak password led to the devastating collapse of KNP Logistics, a 158-year-old UK transport company, after it fell victim...
What is the new 7-Zip vulnerability CVE-2025-53816 and ...
A newly discovered memory corruption vulnerability in 7-Zip, tracked as CVE-2025-53816, allows attackers to craft malicious RAR5 a...
What are the best ways to protect online video calls fr...
In 2025, online video conferencing remains an essential part of work, education, and communication—but also a key target for cyber...
What are the major cybersecurity threats to watch out f...
In 2025, the cybersecurity landscape is dominated by advanced threats such as AI-powered phishing, supply chain attacks, deepfake ...
What happened in the June 2025 WestJet cyber attack and...
In June 2025, Canadian airline WestJet experienced a cyber attack that caused disruptions to its website and mobile app. While fli...
What is the Fortinet FortiWeb CVE-2025-25257 vulnerabil...
The CVE-2025-25257 vulnerability is a critical SQL injection flaw found in Fortinet’s FortiWeb web application firewall. Actively ...
What are the best ways to detect and stop AI-driven cyb...
AI-driven attacks are rapidly evolving, using technologies like deepfakes, voice cloning, and synthetic profiles to deceive employ...
What is the Lenovo Protection Driver Vulnerability CVE-...
The Lenovo Protection Driver vulnerability (CVE-2025-4657) is a buffer overflow flaw found in multiple Lenovo applications, includ...
What is China's Massistant surveillance tool and how do...
Massistant is a mobile surveillance tool developed by SDIC Intelligence (formerly Meiya Pico), used by Chinese law enforcement to ...
What Are the Latest Sophos Intercept X for Windows Vuln...
Three high-severity vulnerabilities—CVE-2024-13972, CVE-2025-7433, and CVE-2025-7472—have been discovered in Sophos Intercept X fo...



















![Top 10 Ethical Hackers in the World [2025]](https://www.webasha.com/blog/uploads/images/202408/image_100x75_66c2f983c207b.webp)


![[2025] Top 100+ VAPT Interview Questions and Answers](https://www.webasha.com/blog/uploads/images/image_100x75_6512b1e4b64f7.jpg)







