What was the recent Microsoft server hack and how did i...
A major cyberattack exploited a zero-day vulnerability in Microsoft SharePoint servers, affecting nearly 100 organizations worldwi...
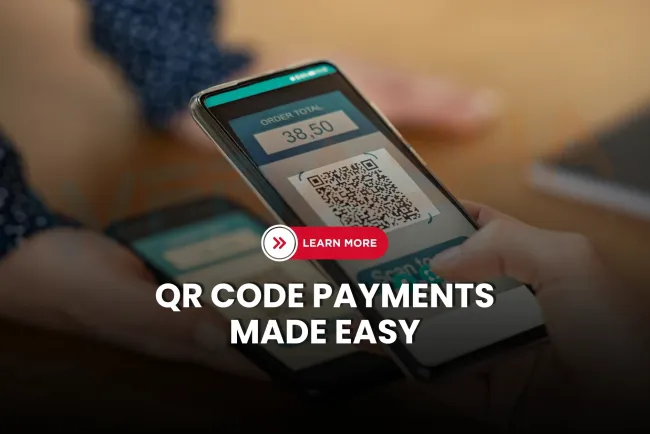
What is 'Scan to Pay' and how does it work step-by-step...
Scan to Pay is a digital payment method where users scan a QR code using a smartphone to instantly pay a merchant. This system use...
How did a weak password lead to the downfall of a 158-y...
A single weak password led to the devastating collapse of KNP Logistics, a 158-year-old UK transport company, after it fell victim...
What is the importance of penetration testing for start...
Penetration testing (pen testing) is crucial for startups in 2025 because it helps detect and fix security vulnerabilities before ...
What is the difference between external and internal pe...
External vs Internal Penetration Testing refers to two different approaches used to assess security vulnerabilities. External test...
What are injection attacks in cyber security and how ca...
Injection attacks in cyber security occur when a hacker sends malicious code through an input field to trick an application into e...
What is the origin of ransomware and how has it evolved...
Ransomware began in 1989 with the AIDS Trojan, a virus that locked files and demanded money via postal mail. Since then, it has ev...
What are the 5 key steps in a cybersecurity incident re...
An effective cybersecurity incident response plan includes five key steps: Preparation, Identification, Containment, Eradication &...
What’s the difference between a pentester and a securit...
A pentester (penetration tester) actively tests and simulates cyberattacks on systems to find vulnerabilities, while a security re...
What is the new 7-Zip vulnerability CVE-2025-53816 and ...
A newly discovered memory corruption vulnerability in 7-Zip, tracked as CVE-2025-53816, allows attackers to craft malicious RAR5 a...
How to Remove Ransomware and Decrypt Files Without Payi...
Learn step-by-step how to remove ransomware and decrypt your files without paying a ransom. Explore real-world tools, best practic...
What are the best ways to protect online video calls fr...
In 2025, online video conferencing remains an essential part of work, education, and communication—but also a key target for cyber...
What are the common types of network and application at...
Network and application attacks are becoming more advanced in 2025, targeting vulnerabilities in servers, APIs, web apps, and clou...
What are the major cybersecurity threats to watch out f...
In 2025, the cybersecurity landscape is dominated by advanced threats such as AI-powered phishing, supply chain attacks, deepfake ...
What happened during the Aflac social engineering cyber...
In June 2025, U.S. insurance provider Aflac fell victim to a sophisticated social engineering attack, believed to be carried out b...
























![Top 10 Ethical Hackers in the World [2025]](https://www.webasha.com/blog/uploads/images/202408/image_100x75_66c2f983c207b.webp)







